English version of the Guide
Reveton virus or Trojan:Win32/Reveton.N Virus or Metropolitan Police virus belongs to a category of Trojan viruses that is known as Ransomware.Invades poorly protected computers who visit often infected websites tricking the user into running an executable file.
After that installs into your system at start up and displays a desktop image pretending the police authority threatens the user into paying a fine or being prosecuted for "naughty habits".
In some cases it contains voices message if you have a mic open and if you have a web cam, a footage with your face, in order to convince you that this is serious business...
Reveton inner workings
In order to fight virus you have to understand him first.Specifically, on execution Reveton Trojan virus does the following
- It installs it's executable in a nice place such as windows folder or in Windows 8 in Users/%username%/ folder
- Creates a shortcut to virus executable in windows startup folder
- Alters the registry
Solution
- Close your Computer from the button (brute shut down)
- Start your computer and hit the F8 key during boot process, until boot menu shows up
- Choose Starting Windows in Safe Mode with command line
- This will place you into a command line black window like the following
 |
| Safe mode command line (in XP) |
4.1 If you are an XP User this .lnk file will be in C:\Documents and Settings\%USERNAME%\Start Menu\Programs\Startup
4.2 If you are an Vista User this .lnk file will be in C:\users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Startup
4.3 If you are an Windows 7 User this .lnk file will be in C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
and
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup
4.4 If you are an Windows 8 User this .lnk file will be in C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
(Notice : where %USERNAME% is your own username e.g. John, Vasilo4ever, Elafrokynhgos, etc.
If you are not sure about what Windows version you run do the following. In command line window write
SET and press <ENTER>
This will print on screen the environment variables
Locate the APPDATA Variable and write down the path. compare to the paths from the 4.1-4.4 points to determine your operating system path, Also, Locate the USERNAME Variable and write it down this is the string you will put in paths instead of %USERNAME%)
5. Now, according to your operating system write in Command line the following
5.1.1 For Windows XP (English)
CD C:\Documents and Settings\%USERNAME%\Start Menu\Programs\Startup
OR
5.1.2 For Windows XP (Greek)
CD C:\Documents and Settings\%USERNAME%\Start Menu\Προγράμματα\Εκκίνηση
For Windows Vista write
CD C:\users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Startup
For Windows 7 write
CD C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Window s\Start Menu\Programs\Startup
For Windows 8 write
CD C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Notice. Be sure you are in the new directory before you proceed if system gives you error means you spell wrong something
6. Write the command
DIR and press <ENTER>
7. Pay attention to the name of the files with extension .lnk. The rogue shortcut file will have a random strange name e.g. such as 1.044OPLSrt.lnk
This is your first target, You must first decipher it and then delete it with all other .lnk files.
8. Insert any USB memory stick you have available in your computer. Try to find its volume letter It maybe E or F or G depending if your computer have a second disk a CD rom or two Try to find your USB writing in command line the following,
E: and press <ENTER>
if this works it will appear the E:> directory otherwise you get a no such directory or filename. you can try (F: or G:)
write DIR and press <ENTER> to see if this is really the USB memory stick.
9. Now we must copy the rogue shortcut .lnk file (say
1.044OPLSrt.lnk) to the USB in order to analyze it in another computer and find the name and path of the infection file. To do this try the commands
1.044OPLSrt.lnk) to the USB in order to analyze it in another computer and find the name and path of the infection file. To do this try the commands
C: <ENTER>
copy c:1.044OPLSrt.lnk to e:badass.lnk <ENTER>
E: <ENTER>
dir <ENTER>
Now spot the badass.lnk you copied in your USB memory stick.
Once you have it remove it
10. Find another computer open it put the USB memory stick in
and copy the badass.lnk to the PC Desktop Surface.
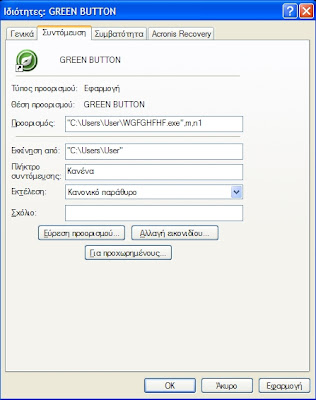
11. Right click on Badass link and choose properties a similar as the following information dialogue in your language will be presented to you
This is the name and place of the enemy in your infected PC. Write down the info of the path and name in a paper.
12. Return to the infected PC and do the next
write in command line
C: and press <ENTER>
Be sure you are at the startup path,
use the command DIR to see the rogue file (lets say your infection shortcut is 1.044OPLSrt.lnk) and write the command
DEL 1.044OPLSrt.lnk <ENTER>
Use DEL in the same manner to clean every .lnk file in startup folder if you want to be safe.
13. Now we go clean the registry write the command
REGEDIT and press <ENTER>
the following window will appear (in your language)
Click in my computer folder
Now select edit from the menu and then find. In the dialogue put the name of the infection file. like this
be sure you check Keys, values, data and press find button
The registry editor will search until finds the first match.
Be very careful and look first at the right pane there is the infection point with the infection's executable name. Now look carefully at the left pane. This is the registry tree.
The folder you have to delete is the one that is open, The name of the folder is 'parameters' and it is a subfolder to a folder with a name such as 'Winmngt'.
Now click in the left panel, the folder above the folder named parameters, the lets say Winmngt folder and delete it by pressing <DEL> button
You now continue the search by pressing F3.
Each time you find infection registry entry you delete you as described above.
14 After you finish the search in registry close the Registry editor window and press <ALT><CTRL><DEL> and shutdown your computer
15. Boot your computer again and press repeatedly <F8>.
Enter in Safe mode with command line
16. Now, it's payback time. You will eradicate the infection executable once and for all. At command line and according to your system. Read the piece of paper you wrote the path of the executable. Read it and delete it with DEL command e.g. in Windows 8 the command line will look like
DEL /F/Q C:\USERS\User\WGFGHFHF.EXE <ENTER>
Now shutdown and restart and you are free.
No Ransoms paid no hostages taken!
Now you have to secure your PC and scan your system for Trojans and back doors that will reinfect your system to get rid of them.
Go to
http://www.sophos.com/en-us/products/free-tools/virus-removal-tool.aspx
and download their tool. This will scan your system for viruses and will clean your system.
It will take hours to scan your system BUT after that you are going to be safe from reinfections.
Now you have to secure your PC and scan your system for Trojans and back doors that will reinfect your system to get rid of them.
Go to
http://www.sophos.com/en-us/products/free-tools/virus-removal-tool.aspx
and download their tool. This will scan your system for viruses and will clean your system.
It will take hours to scan your system BUT after that you are going to be safe from reinfections.





1 comment:
kz445 vivobarefoot shoes,vionic スニーカー,etnies shoes,danner polska,gabornz,saucony スニーカー,timberland mexico,scarpeheydude,clarks hungary jq606
Post a Comment